Buy and Sell in Honiara | Round table full solid vasa if u nidim just contact 8646508 or cam lukim mipala lo ADS Quality Furniture (Ranadi) | Facebook

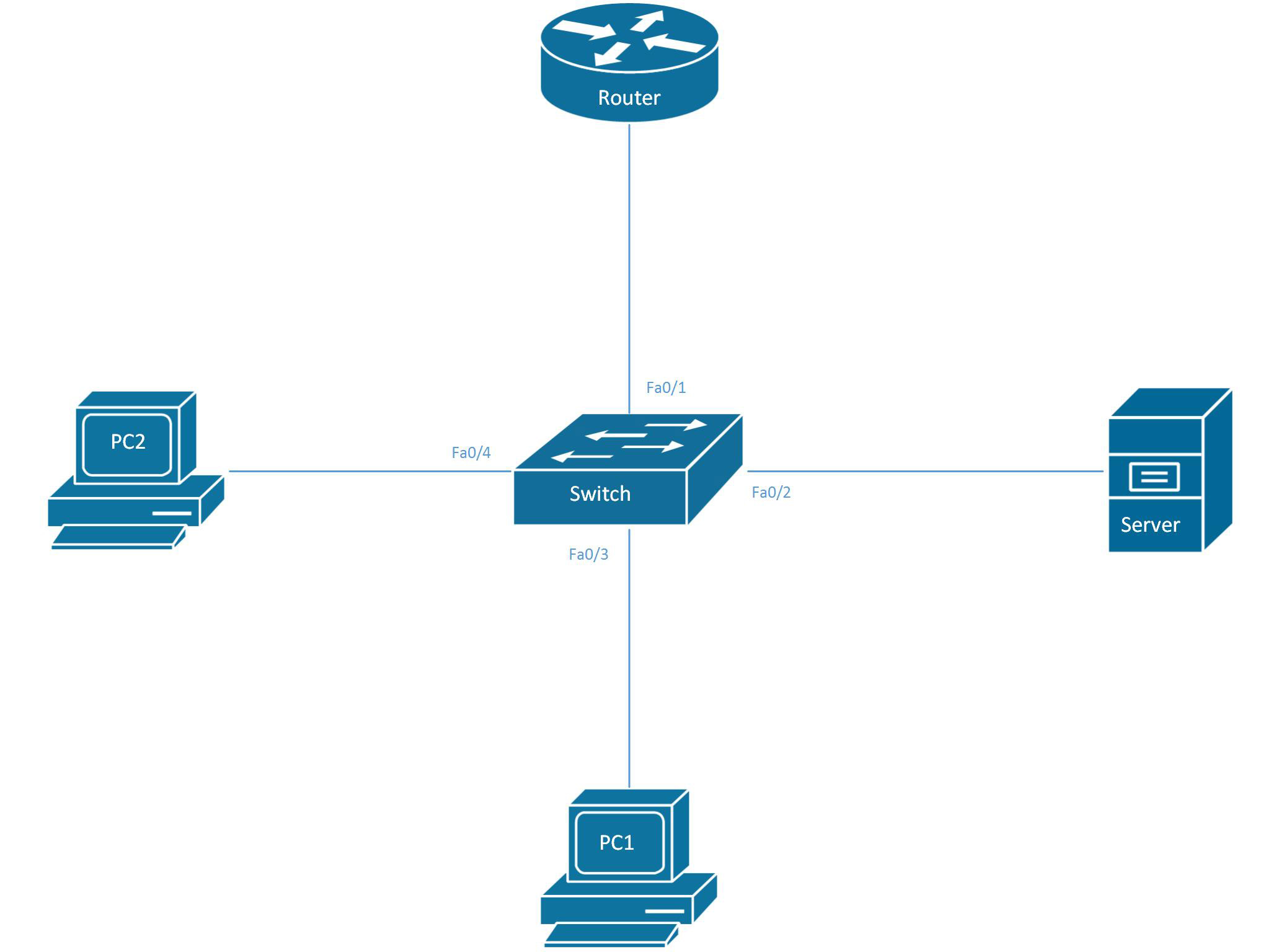
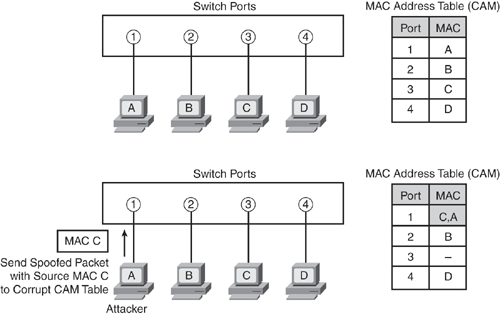
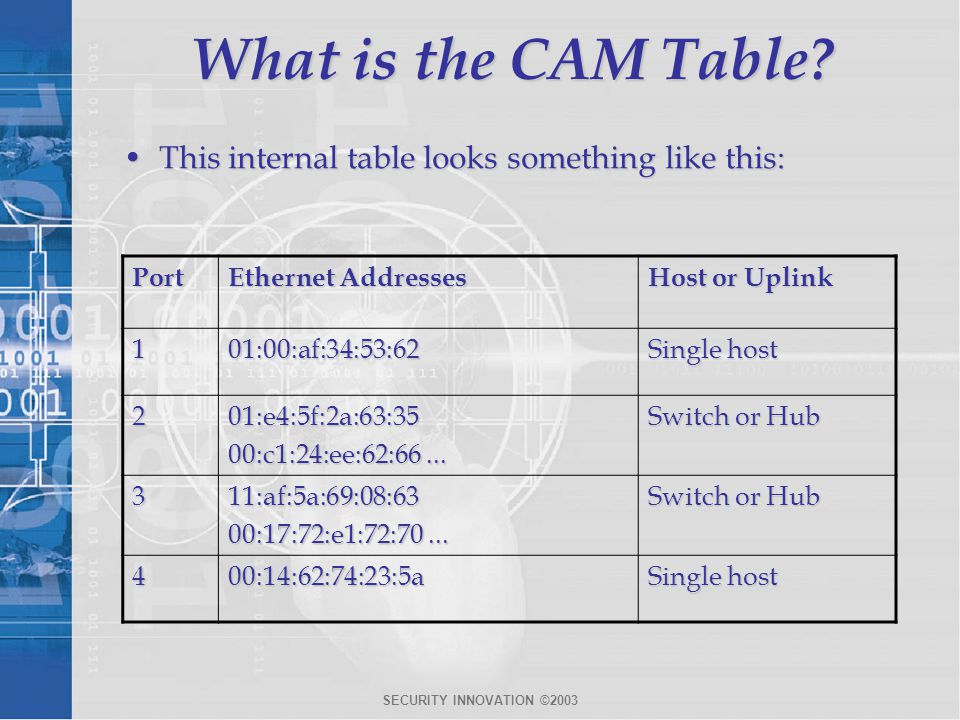
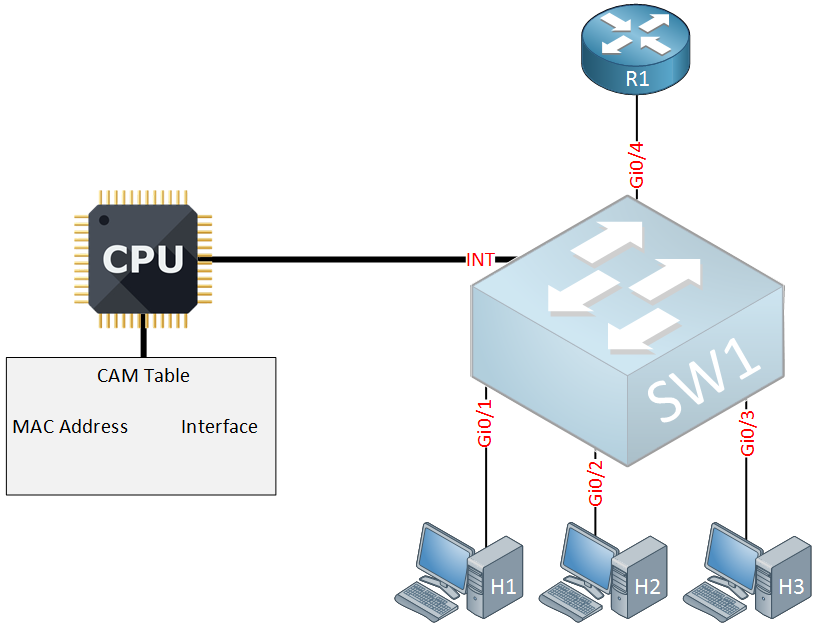
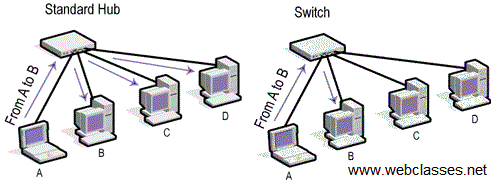
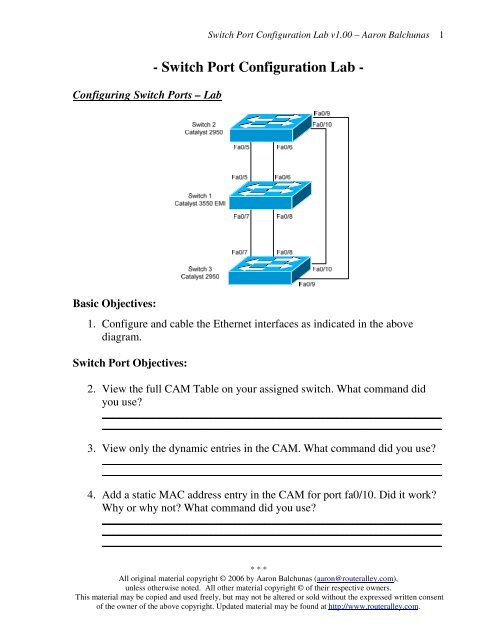
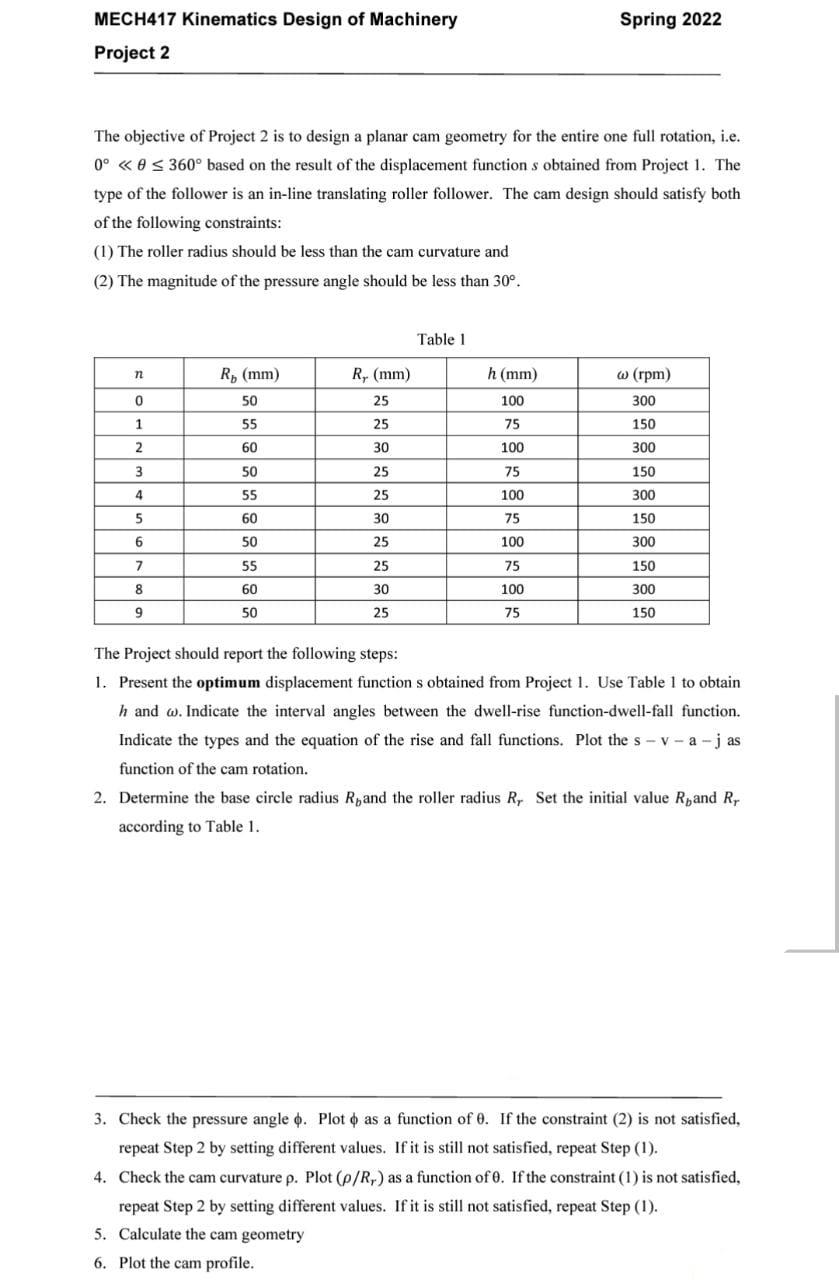
Design and analysis of data link impersonation attack for wired LAN application layer services | SpringerLink

Cambro Cam GoBox® Black Top Loading EPP Insulated Food Pan Carrier - 8" Deep Full-Size Pan Max Capacity